Spooldr Rootkit (ecard.exe) removal story
UnHackMe detects the working driver (not hidden) during the "Scan for Viruses" process:
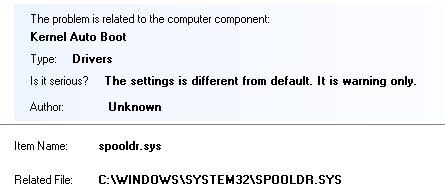
Also it detects the open process immediately after reboot:
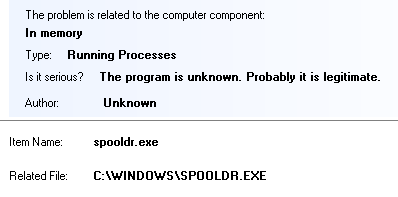
But the spooldr.exe file is hidden by rootkit technology.
I used the Bootlog XP software to track the boot process. I found that the spooldr.sys is started immediately after "%SysDir%\Drivers\tcpip.sys".
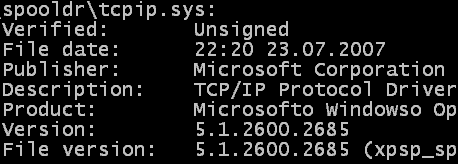
I checked the file sign of the tcpip.sys and I found that it is not signed. However the original tcpip.sys is signed.
I discovered the contents of the "tcpip.sys" and found the string "spooldr.sys" in the end of the file.
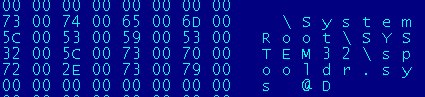
The virus in the TCPIP.SYS is used for loading "spooldr.sys" driver.
After that the driver executes "spooldr.exe" and hides the executable file.
Spooldr.exe is used for propagation.
UnHackMe detects the "spooldr.sys" driver and it removes the driver at the next reboot. After that we can simply delete spooldr.exe and restore old tcpip.sys in the %SysDir%\Drivers and in the %SysDir%\dllcache folders.
In addition, we need to remove "spooldr.exe" from the Windows Firewall Exclusion list.
Also, delete the "spooldir.ini" from "Documents and Settings\UserName" fodler.
System requirements
Windows 9x, 2000/2003/XP/2008/Vista/Seven or higher 32 or 64 bit.512 Mb RAM
CD/DVD drive or USB stick.
Purchase now!
Purchase includes:
• UnHackMe Single License - Electronic Delivery
• Warrior CD Image - Electronic Delivery
People say:
LisaThis solution works great. Thanks!
Jim
Works as advertised. Keep up your good work guys!
