|
Registry Tracer monitors selected registry keys, and advises of changes. It allows you to reverse any modifications, additions, or deletions.
|
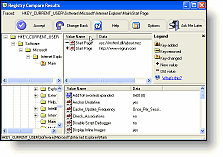
You will see the "Registry Compare Results" window when the changes found.
- If a new key was added - it will show a ′+′
- If a new key was deleted - it will show a ′-′
- If an existing key was modified it will show a ′?′
All you do is click the key and you will see the added, deleted or modified values in the right panel.
Click on the "What′s this" button to get information about monitored registry key or send a request to support team.
