I tested the sample rootkit file and I found that it′s hardly hidden than other known rootkits. The lzx32.sys driver is loaded by the system at the early part of Windows boot. It′s masked as the boot device. This why it′s hard in removal.
UnHackMe 4 (with Partizan) detects the rootkit keys but it could not remove Rustock.
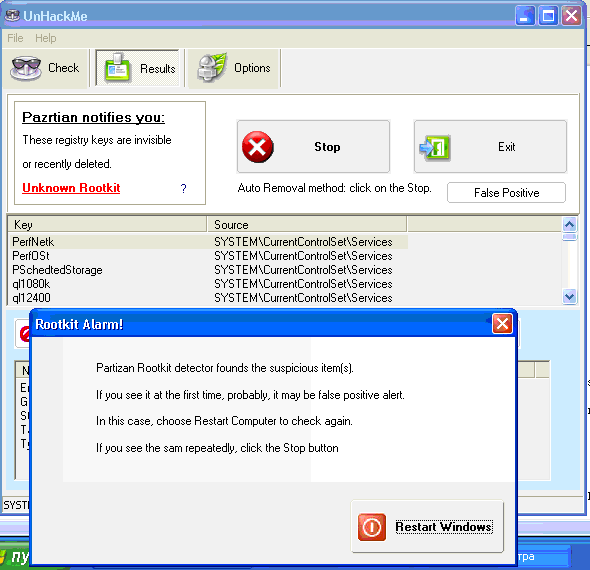
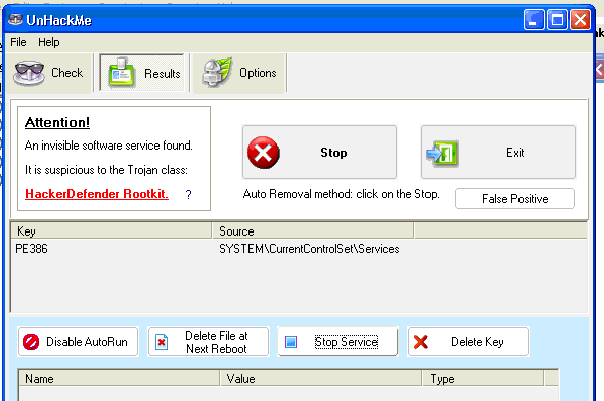
The driver is located in the NTFS stream in the %Windir%\System32:lzx32.sys.
It could not be deleted during Windows normal mode.
No panic!
I found the simple way how to stop Rustock :-).
Unzip it to any folder. Installation is not required.
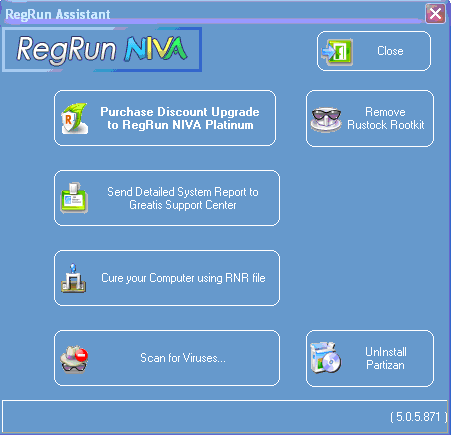
After finishing removal process you may remove Partizan from your Windows boot.
Click on the "UnInstall Partizan" button.
Also you can delete "RootkitNo" folder from your drive where installed the Windows.

|
Good luck!
Dmitry Sokolov |